Version 1.664
Released: 2024-06-05
Template for auto security.txt file new
The contents of auto-generated security.txt are now loaded from a template that can be customized. Template location is ./data/templates/security.txt, it uses the main user account email as the contact point.
The following variables can be used inside the template.
Generic:
EXPIRES- expected file expiration time (one month into the future from the current time).HOST- domain or subdomain for which security.txt file is rendered.SERVERNAME- server host name.
Information related to the user account that owns the domain or sub-domain:
USERNAME- account login name.REAL_NAME- full name stored in user config.EMAILADDRESS- email address associated with user account.DEFAULT_DOMAIN- default user domain.USERLANG- preferred language code.USERTYPE- user access level, one ofuser,reselleroradmin.USERPACKAGE- name of the user package used with this user account.USERCREATOR- admin or reseller account name that owns this used account.
Information about the user account creator (usually reseller but can be an admin as well if admin):
RESELLER_USERNAME- account login name.RESELLER_REAL_NAME- full name stored in user config.RESELLER_EMAILADDRESS- email address associated with the account.RESELLER_DEFAULT_DOMAIN- default reseller domain.RESELLER_LANG- preferred language code.
The template also has access to all custom domain items via variables.
Example template that uses a reseller email address as the main contact for security related reports:
Contact: mailto:|RESELLER_EMAILADDRESS|
Expires: |EXPIRES|
Example template that uses a fixed server-wide email address:
Contact: mailto:security@|SERVERNAME|
Expires: |EXPIRES|
Having a template also gives much flexibility for adding additional information to the secutity.txt contents.
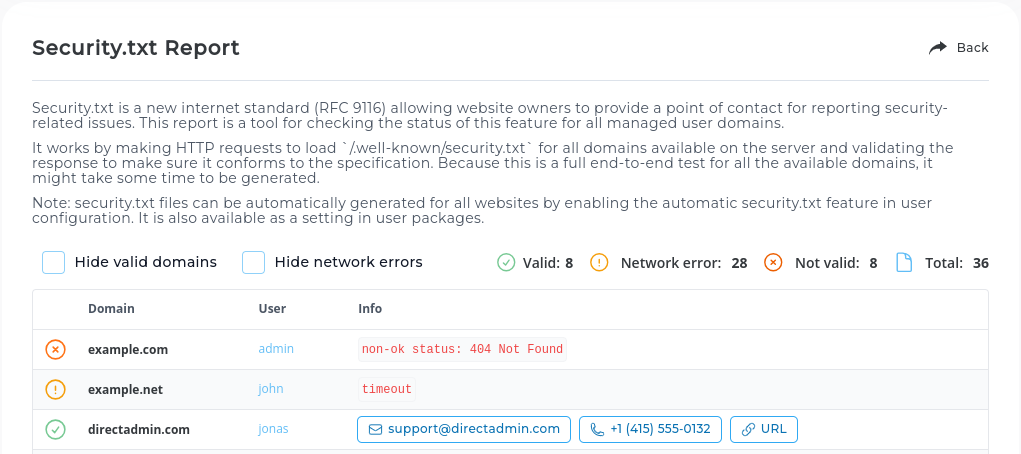
Security.txt report new
A new page called Security.txt Report is now available for Reseller level and Admin level accounts. It reports security.txt (RFC 9116) compliance and availability for all the domains.
Support for MySQL 8.4 new
This release extends DA to support MySQL 8.4. This version is the next LTS release.
TLS certificate caching in directadmin web service new
The DirectAdmin web server is updated to cache server and domain certificates. This adds a small speed improvement for all requests to the control panel when TLS is enabled.
Older versions used to read TLS certificates from disk on each HTTP request.
The cache is automatically updated if certificate files are replaced. The cache is also flushed if directadmin service receives a SIGHUP signal.
Maintenance task for old_public_html_link deprecation new
A new maintenance task is added to help prepare for the old_public_html_link configuration option removal. This task changes old_public_html_link to be enabled, and changes ~/public_html to be a symlink to the user's default domain document root.
Upgraded database restore from backup logic update
User account backups include information about user owned-databases, database user accounts, and database contents. Part of the backup restore logic that restores databases received a major upgrade. Here is the list of notable improvements.
Improved security. Database data (SQL queries to restore data) is always executed in the process running as the user that is being restored. Connections to the database are made using temporary credentials having access only to the database that is being restored. Older versions used an account with SUPER privileges to perform the restore operation. This required trusting that backups were not tampered with by adding malicious SQL statements. The new restore logic allows the complete removal of restore_database_as_admin configuration parameter from directadmin.conf.
Improved compatibility. Database backups can include advanced DB features like triggers, views, events, functions, and procedures. The restore operation will ensure advanced objects are restored and will make sure to automatically fix all definer related permissions issues. Older versions were not able to restore everything on user-level restore operations, and admin-level restore operations could produce missing definer problems after restore.
Improved reliability. Database restore no longer uses the source command and always correctly reports data restore errors. The new restore logic allows the complete removal of abort_source_on_error configuration option from directadmin.conf. The restore operation no longer uses temporary password changes. A dedicated temporary user account is used instead.
Configuration of server host name certificate renewal update
Server host name TLS certificate management using ACME (automatic certificates from LetsEncrypt or ZeroSSL) received a major upgrade.
ACME configuration is now explicitly defined in the directadmin.conf file using new configuration options:
acme_server_cert_enabled- enables automatic certificate renewal using ACME.acme_server_cert_provider- certificate provider (letsencryptorzerossl) to use for server TLS certificate, when empty the default provider will be used.acme_server_cert_key_type- key type and size of the server certificate.acme_server_cert_account- email address used for ACME account, if empty default admin email address will be used.acme_server_cert_additional_domains- a list of additional domain names to be included in the certificate (the server host name is always included).acme_server_cert_dns_provider- DNS provider name if DNS challenge is used, and the server does not control the server host name zone.acme_server_cert_dns_provider_env_file- file with additional parameters when a custom DNS provider is used.
Configuration will be automatically detected and updated during the upgrade.
This release introduces new API endpoints for server host name certificate management. Certificate management integration in the UI is expected in the upcoming releases.
Custom character set when creating DB via API update
API endpoints that create a new database are extended to support providing a custom default character set for the new database. Endpoints affected:
POST /api/db-manage/create-dbPOST /api/db-manage/create-db-with-user
Earlier versions only supported custom collation. Specifying a custom character set is optional. If not provided server, then server default will be used.
Software version changes custombuild update
MySQL 8.4added with8.4.0versionphalcon5updated from5.6.2to5.7.0roundcubemailupdated from1.6.6to1.6.7nginxupdated from1.26.0to1.27.0mod_lsapiupdated from1.1-72to1.1-73imagemagickupdated from7.1.1-32to7.1.1-33ioncube_loadersupdated from13.0.2to13.0.4PHP 8.1updated from8.1.28to8.1.29PHP 8.3updated from8.3.6to8.3.8PHP 8.2updated from8.2.18to8.2.20modsecurity_owasp_rulesupdated from4.2.0to4.3.0MariaDB 10.4updated from10.4.33to10.4.34MariaDB 10.5updated from10.5.24to10.5.25MariaDB 10.6updated from10.6.17to10.6.18MariaDB 10.11updated from10.11.7to10.11.8
Exim server hostname auto-detection update
On some servers (RHEL based systems, having IPv6 stack enabled and using a short host name) exim was unable to reliably detect server FQDN. This leads to email delivery problems and exim using only the server name instead of FQDN in HELO messages.
In this release exim.variables.conf file is extended to explicitly inform exim of the server hostname instead of relying on auto-detection.
Cleanup database when removing WordPress update
The WordPress removal action is extended to automatically clean up the database. The database and its users are removed only if the database is left empty after WordPress removal. External databases are left untouched (databases not managed by DirectAdmin).
File /etc/services in jailshell environment update
The jailshell environment is updated to have /etc/services file. This file provides a mapping between service name and numeric TCP/UDP port. Some CLI tools does not work properly when this file is missing. One such example is ftp command.
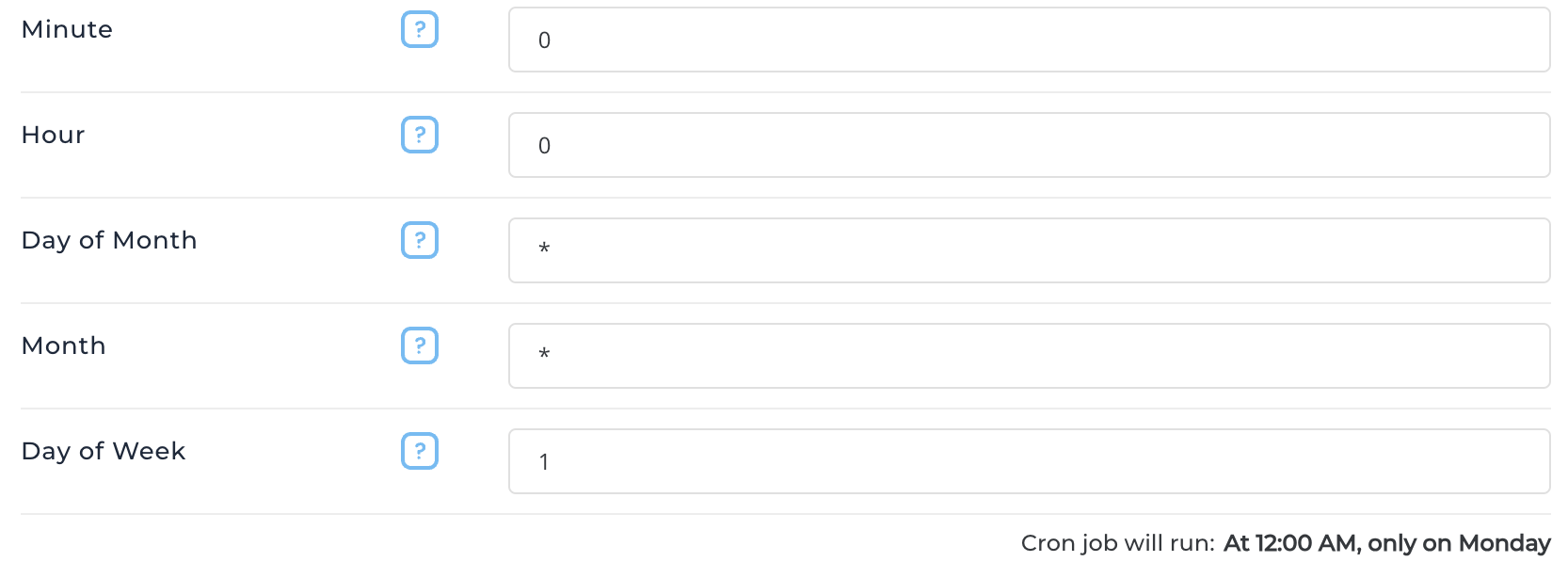
Cron input hints evolution update
All pages that create cron jobs will now show a message that lets the user know when a cron task is scheduled to run.
The screenshot below is an example from the cron job creation page (user level -> Advanced Features -> Cron Jobs).
Increased user package name length limit evolution update
The maximum length of the user package name is increased from 20 to 64 symbols.
DMARC alignment for auto-generated emails fix
Emails generated by the mail server (vacation messages and auto-responders) used to use the server host name for DKIM signing. This causes problems delivering these emails to servers using strict DMARC alignment checks (for example gmail).
Exim configuration was updated to use DKIM key of the domain email originates from instead of server hostname.
All SSL Request keys will be backed up into User's home fix
Possible race condition with AutoSSL and User Certificate Request (CSR), where the CSR key might go through, only existing in the DirectAdmin data directory, and where the AutoSSL completes after this, overwriting the only instance of the CSR. All CSR keys will have a copy in the User's home, example:
~/.ssl_keys/domain.com-secp384r1-bit.CSR.1715711017.key
where the filename includes the key-type, as well as the unix timestamp when it was created.
Rspamd email whitelist and blacklist filters fix
Rspamd whitelist and blacklist email filters are case insensitive but are still expected to be in lowercase in configs.
Rspamd config generator is updated to always save emails in lowercase.
Resellers unable to override TTL fix
Resellers were not able to override TTL for their own owned domains' DNS records. This issue is now resolved.
NS and PTR records are no longer shown if they're not enabled evolution fix
Within the user level DNS page (Account Manager -> DNS Management) it was possible to add NS or PTR records when they were set to 1 in directadmin.conf (dns_ns=1 for NS records or dns_ptr=1 for PTR records).
Now you can only select these records to be added when the appropriate settings are set to 2. Additionally, they no longer show up in the table unless the same condition is met.
Reseller level resource limit hits page does not display data evolution fix
The reseller-level resource limit hits page (System Info & Files -> Resource Limits -> Limit Hits -> user name) now displays data within the table. It used to throw an error and show an empty table before.
Custom feature set translations evolution fix
Translations for custom feature set names were not being displayed. Now, these translations will be correctly shown.
Create buttons are now hidden when the limit is reached evolution fix
When the limit is reached, the Create buttons in the page header will be hidden. This affects Forwarders, Domain Pointers, Domains, and Autoresponders pages. This change provides a clearer indication that the limit has been reached, and no further items can be created until some are removed or the limit is increased.
Login key log with IPv6 entries fix
Checking login key access log used to incorrectly split the IP address column for entries with IPv6 addresses.
The issue is fixed and full IPv6 address is now shown in the IP column.
No longer generate DLV records when using dnssec.sh removal
With the discontinuation of ISC DLV Registry, generating DLV records is no longer needed. The script dnssed.sh will no longer generate DLV records.
Removed docsroot configuration option removal
Configuration option docsroot is removed from directadmin.conf. This option is replaced with new system_skin option.
Removed restore_database_as_admin configuration option removal
The configuration option restore_database_as_admin is removed from directadmin.conf. Databases are always restored using the privileges of the account that is being restored. This option is no longer needed since new restore mode does not require SUPER privileges to restore databases.
Removed abort_source_on_error configuration option removal
The configuration option abort_source_on_error is removed from directadmin.conf. Client side source command is no longer used when restoring databases.
Removed license configuration option removal
The configuration option license is removed from directadmin.conf. It used to allow setting custom location of the license file. Starting this release a fixed location /usr/local/directadmin/conf/license.key is used unconditionally.
